
Nairaland Pulse | News

Анатолий Шарий

Реальний Київ | Украина

Мир сегодня с "Юрий Подоляка"

Труха⚡️Україна

Николаевский Ванёк

Инсайдер UA

Реальна Війна | Україна | Новини

Лачен пише

Nairaland Pulse | News

Анатолий Шарий

Реальний Київ | Украина

Мир сегодня с "Юрий Подоляка"

Труха⚡️Україна

Николаевский Ванёк

Инсайдер UA

Реальна Війна | Україна | Новини

Лачен пише

Nairaland Pulse | News

Анатолий Шарий

Реальний Київ | Украина

Rafa Sec
Hey I'm Rafu 👋
Cybersec enthusiast | bughunter | Ethical hacker | CTF player
Feel free to join😊
-> you can contact me in @Rafa_support
- Join chat: @rafasec_chat
- join course channel: @Rafa_course
Cybersec enthusiast | bughunter | Ethical hacker | CTF player
Feel free to join😊
-> you can contact me in @Rafa_support
- Join chat: @rafasec_chat
- join course channel: @Rafa_course
关联群组
Rafa Sec Community
135
记录
17.05.202523:59
372订阅者03.04.202523:59
0引用指数30.04.202521:01
847每帖平均覆盖率24.04.202521:01
847广告帖子的平均覆盖率02.05.202523:59
18.25%ER25.04.202503:53
305.78%ERR
01.05.202517:16
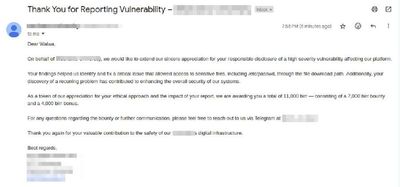
We made it again! 💥 Another 11K birr! 💸
This all happened because of 3 things:
1️⃣ God 🙏
2️⃣ My mentor Nathan 👨🏫 @geeztechgroup
3️⃣ My hard work 😂💻
#Blessed #GrindPays #BugBountyWin
@rafa_sec
This all happened because of 3 things:
1️⃣ God 🙏
2️⃣ My mentor Nathan 👨🏫 @geeztechgroup
3️⃣ My hard work 😂💻
#Blessed #GrindPays #BugBountyWin
@rafa_sec


09.05.202507:19
🔒🔥 Security Bug Found – Account Takeover & Privilege Escalation 🔓
💰 Reward: 23,000 BIRR
While testing a web app, I discovered a serious mass assignment vulnerability.
📌 Here’s how I found it:
During password change, the request sent:
I changed it to:
✅ Result: The password for both accounts got updated!
Later, I saw:
I changed it to:
✅ My account became an admin.
🧠 What I achieved:
✅ Account Takeover (ATO) via Password Change
✅ Privilege Escalation via Mass Assignment
💸 This bug earned me 23,000 BIRR from the program.
Always validate and sanitize input on the server side!
@rafa_sec
💰 Reward: 23,000 BIRR
While testing a web app, I discovered a serious mass assignment vulnerability.
📌 Here’s how I found it:
During password change, the request sent:
"email": "email@example.com"I changed it to:
"email": ["email1@example.com", "email2@example.com"]✅ Result: The password for both accounts got updated!
Later, I saw:
"role": "user"I changed it to:
"role": "administrator"✅ My account became an admin.
🧠 What I achieved:
✅ Account Takeover (ATO) via Password Change
✅ Privilege Escalation via Mass Assignment
💸 This bug earned me 23,000 BIRR from the program.
Always validate and sanitize input on the server side!
@rafa_sec
08.05.202518:00
🚨💥 New Bounty Is Coming... 🐞
Stay tuned, something wild just got caught! 👀💻
@rafa_sec
Stay tuned, something wild just got caught! 👀💻
@rafa_sec


14.05.202513:51
@rafa_sec


30.04.202519:26
I identified a critical security issue 🚨 where sensitive credentials were exposed through source code 🧑💻🔓 — received a reward of 11,000 birr 💰
@rafa_sec
@rafa_sec
06.05.202518:53
Zesiano's wisdom: 🤔
Hacking is about creativity, not tools. Spend 90% thinking 🧠, 10% scanning. 💻🔑
@rafa_sec
Hacking is about creativity, not tools. Spend 90% thinking 🧠, 10% scanning. 💻🔑
@rafa_sec
11.05.202518:13
Password: @rafa_sec
instalization:
1.
2.
instalization:
1.
./set-permissions.sh
2.
sudo docker-compose up


15.05.202518:37
👀😁
@rafa_sec
@rafa_sec
07.05.202505:14
Good morning guys ❤️
05.05.202508:16
🚀 eWPTv2 Course: Become a Web App Pentesting Pro! 🚀
Ready to launch your career in web application security? This Intermediate Level course is your fast track to mastering practical pentesting skills! 🎯
Course Highlights:
• Web App Security Fundamentals 💡
• Information Gathering 🔎
• Authentication & Authorization Testing 🔑
• Injection Attacks 💉
• File Inclusion Vulnerabilities 📄
• Server-Side Request Forgery (SSRF) 🌐
• Web Services Security ⚙️
• Practical Exploitation Techniques 🛠
• Hands-On Labs 🧪
• Report Writing 📝
Key Benefits:
• 🔥 Hands-On Learning: Real-world scenarios and practical exercises.
• ✅ Certification Prep: Ace the eWPTv2 exam with confidence.
• 📈 Career Advancement: Boost your skills and earning potential.
• 🛡 Real-World Skills: Protect web apps with cutting-edge techniques.
Join now and start your journey to becoming a Best web application penetration tester! ✨➡️ click this for course
💬 Chat: @rafasec_chat
📢 Channel: @rafa_sec
📚 Course Updates: @rafa_course
Ready to launch your career in web application security? This Intermediate Level course is your fast track to mastering practical pentesting skills! 🎯
Course Highlights:
• Web App Security Fundamentals 💡
• Information Gathering 🔎
• Authentication & Authorization Testing 🔑
• Injection Attacks 💉
• File Inclusion Vulnerabilities 📄
• Server-Side Request Forgery (SSRF) 🌐
• Web Services Security ⚙️
• Practical Exploitation Techniques 🛠
• Hands-On Labs 🧪
• Report Writing 📝
Key Benefits:
• 🔥 Hands-On Learning: Real-world scenarios and practical exercises.
• ✅ Certification Prep: Ace the eWPTv2 exam with confidence.
• 📈 Career Advancement: Boost your skills and earning potential.
• 🛡 Real-World Skills: Protect web apps with cutting-edge techniques.
Join now and start your journey to becoming a Best web application penetration tester! ✨➡️ click this for course
💬 Chat: @rafasec_chat
📢 Channel: @rafa_sec
📚 Course Updates: @rafa_course
24.04.202508:36
199😳
Sudo apt install 1 member 😁
Sudo apt install 1 member 😁


18.04.202511:53
ነገር ግን እኛ ኀጢአተኞች ሳለን ክርስቶስ ስለ እኛ ሞተ፤ ይህም እግዚአብሔር ለእኛ ያለውን የራሱን ፍቅር ያሳያል።
ሮሜ 5:8
መልካም በአል🙏❤️
@rafa_sec
ሮሜ 5:8
መልካም በአል🙏❤️
@rafa_sec
24.04.202510:41
RafaCTF – Web CTF Lab (Free & Online)
Hey hackers!
I’ve launched RafaCTF, a custom Capture The Flag (CTF) lab where you can practice real-world web vulnerabilities across 4 difficulty levels — from Easy to Insane!
What’s Inside?
🛡️ 7 Vulnerability Categories:
1. ⚔️ XSS (Cross-Site Scripting)
2. ⏱️ Rate Limit Bypass
3. 🔐 Brute Force
4. ✍️ Content Injection
5. 🧩 HTML Injection
6. ⚙️ JavaScript Injection
7. 🕵️ XSSI (Cross-Site Script Inclusion)
Features:
✅ 4 difficulty levels per challenge
✅ Hidden flag in each level
✅ Beginner-friendly & self-hosted
✅ Learn while hacking — hands-on!
Flag Path Format:
/flags/<vuln_name>/level1.txt (…up to level4.txt)
Try it. Hack it. Learn it.
Website: http://rafasecctf.rf.gd/
Need help or want to share your progress?
💬 Chat: @rafasec_chat
📢 Channel: @rafa_sec
📚 Course Updates: @rafa_course
Created by: Rafu | 2025
Hey hackers!
I’ve launched RafaCTF, a custom Capture The Flag (CTF) lab where you can practice real-world web vulnerabilities across 4 difficulty levels — from Easy to Insane!
What’s Inside?
🛡️ 7 Vulnerability Categories:
1. ⚔️ XSS (Cross-Site Scripting)
2. ⏱️ Rate Limit Bypass
3. 🔐 Brute Force
4. ✍️ Content Injection
5. 🧩 HTML Injection
6. ⚙️ JavaScript Injection
7. 🕵️ XSSI (Cross-Site Script Inclusion)
Features:
✅ 4 difficulty levels per challenge
✅ Hidden flag in each level
✅ Beginner-friendly & self-hosted
✅ Learn while hacking — hands-on!
Flag Path Format:
/flags/<vuln_name>/level1.txt (…up to level4.txt)
Try it. Hack it. Learn it.
Website: http://rafasecctf.rf.gd/
Need help or want to share your progress?
💬 Chat: @rafasec_chat
📢 Channel: @rafa_sec
📚 Course Updates: @rafa_course
Created by: Rafu | 2025
06.05.202508:40
Hacking TIP Day1:
Tip1:
Tip2:
Happy hacking and bug hunting! 🐞🔍
💬 Chat: @rafasec_chat
📢 Channel: @rafa_sec
📚 Course Updates: @rafa_course
Tip1:
Start every recon🔍 by mapping the attack surface thoroughly. Use tools like subfinder, httpx, and nmap to discover subdomains, alive hosts, and open ports. A wide recon often reveals hidden or forgotten services that are goldmines for bugs.
Tip2:
Always check for parameter pollution by duplicating query or body parameters (e.g., ?user=admin&user=guest). Some backends may use the first, others the last—leading to unexpected behavior or even auth bypass.
Happy hacking and bug hunting! 🐞🔍
💬 Chat: @rafasec_chat
📢 Channel: @rafa_sec
📚 Course Updates: @rafa_course
07.05.202516:50
🔥 Day 2 - Hacking Tips
🛠 Tip 1:
🔍 Tip 2:
👉 Happy Hacking and Bug Hunting!
@rafa_sec
🛠 Tip 1:
Fuzz for Hidden Parameters
Use tools like ParamMiner to discover hidden parameters like admin=true or debug=1 that can lead to privilege escalation.
🔍 Tip 2:
Check HTTP Method Misuse
Try methods like PUT, DELETE, or OPTIONS on endpoints. Misconfigurations here can expose serious flaws.
👉 Happy Hacking and Bug Hunting!
@rafa_sec
登录以解锁更多功能。
