Анатолий Шарий

Реальний Київ | Украина

Лёха в Short’ах Long’ует

Мир сегодня с "Юрий Подоляка"

Труха⚡️Україна

Николаевский Ванёк

Инсайдер UA

Реальна Війна | Україна | Новини

Лачен пише

Анатолий Шарий

Реальний Київ | Украина

Лёха в Short’ах Long’ует

Мир сегодня с "Юрий Подоляка"

Труха⚡️Україна

Николаевский Ванёк

Инсайдер UA

Реальна Війна | Україна | Новини

Лачен пише

Анатолий Шарий

Реальний Київ | Украина

Лёха в Short’ах Long’ует

cRyPtHoN™ INFOSEC (EN)
Latest news of INFOSEC (EN)
1. Latest Vulnerability.
2. Latest Patch.
3. Privacy Breach.
4. Security Breach.
5. InfoSec News.
German Version 🇩🇪
@cRyPtHoN_INFOSEC_DE
France Version 🇫🇷
@cRyPtHoN_INFOSEC_FR
Italian Version 🇮🇹
@cRyPtHoN_INFOSEC_IT
1. Latest Vulnerability.
2. Latest Patch.
3. Privacy Breach.
4. Security Breach.
5. InfoSec News.
German Version 🇩🇪
@cRyPtHoN_INFOSEC_DE
France Version 🇫🇷
@cRyPtHoN_INFOSEC_FR
Italian Version 🇮🇹
@cRyPtHoN_INFOSEC_IT
TGlist रेटिंग
0
0
प्रकारसार्वजनिक
सत्यापन
असत्यापितविश्वसनीयता
अविश्वसनीयस्थान
भाषाअन्य
चैनल निर्माण की तिथिЛист 27, 2018
TGlist में जोड़ा गया
Лип 01, 2024संलग्न समूह
cRyPtHoN™ INFOSEC (EN) Chat
92
रिकॉर्ड
08.12.202423:59
4.2Kसदस्य08.02.202520:48
1200उद्धरण सूचकांक29.10.202423:59
203प्रति पोस्ट औसत दृश्य07.09.202423:59
176प्रति विज्ञापन पोस्ट औसत दृश्य06.02.202520:16
5.88%ER29.10.202423:59
4.82%ERR
28.04.202514:19
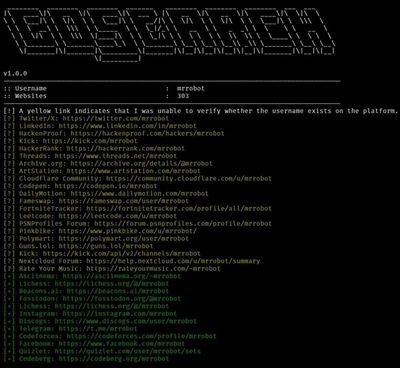
GoSearch: Open-source OSINT tool for uncovering digital footprints
GoSearch is an open-source OSINT tool built to uncover digital footprints linked to specific usernames. Designed for speed and accuracy, it lets users quickly track someone’s online presence across multiple platforms.
https://github.com/ibnaleem/gosearch
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
GoSearch is an open-source OSINT tool built to uncover digital footprints linked to specific usernames. Designed for speed and accuracy, it lets users quickly track someone’s online presence across multiple platforms.
https://github.com/ibnaleem/gosearch
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202508:00
Node.js Vulnerability Enables Attackers to Crash Processes and Disrupt Services
Node.js project has released a critical security update addressing several vulnerabilities that could allow attackers to crash server processes and disrupt critical services.
The security fixes, announced on May 14, 2025 by Node.js maintainer RafaelGSS, affect multiple release lines (LTS and Current) and target issues identified as CVE-2025-23166, CVE-2025-23167, and CVE-2025-23165.
https://gbhackers.com/node-js-vulnerability-enables-attackers-to-crash-processes/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Node.js project has released a critical security update addressing several vulnerabilities that could allow attackers to crash server processes and disrupt critical services.
The security fixes, announced on May 14, 2025 by Node.js maintainer RafaelGSS, affect multiple release lines (LTS and Current) and target issues identified as CVE-2025-23166, CVE-2025-23167, and CVE-2025-23165.
https://gbhackers.com/node-js-vulnerability-enables-attackers-to-crash-processes/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202507:59
Andrei Tarasov: Inside the Journey of a Russian Hacker on the FBI’s Most Wanted List
Once a key figure in the Angler exploit kit underworld, Tarasov’s life has unraveled into detention, paranoia, and an unwanted return to the Russia he publicly despised.
Andrei Tarasov’s criminal life is not as glamorous as you might expect from a leading criminal actor.
Tarasov (aka Aels and more recently Lavander) left his native Russia because of ‘political persecution’; subsequently claiming to have been granted asylum in Ukraine. He was outspoken in his condemnation of modern Russia, saying he removed himself “Because nothing is left from the ‘great’ country I grew up in except for a bunch of clowns and the battle against America…
https://www.securityweek.com/andrei-tarasov-inside-the-journey-of-a-russian-hacker-on-the-fbis-most-wanted-list/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Once a key figure in the Angler exploit kit underworld, Tarasov’s life has unraveled into detention, paranoia, and an unwanted return to the Russia he publicly despised.
Andrei Tarasov’s criminal life is not as glamorous as you might expect from a leading criminal actor.
Tarasov (aka Aels and more recently Lavander) left his native Russia because of ‘political persecution’; subsequently claiming to have been granted asylum in Ukraine. He was outspoken in his condemnation of modern Russia, saying he removed himself “Because nothing is left from the ‘great’ country I grew up in except for a bunch of clowns and the battle against America…
https://www.securityweek.com/andrei-tarasov-inside-the-journey-of-a-russian-hacker-on-the-fbis-most-wanted-list/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv

28.04.202513:49
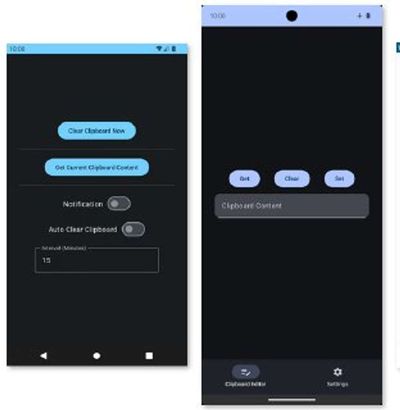
MemoryGuardian
Take Control of Your Clipboard
A Small App for Enhanced Privacy & SecurityMemory Guardian is a lightweight Android app that enhances user privacy and security by automatically clearing the clipboard at set intervals. This helps protect sensitive information, like passwords, from potential leaks to other applications.
https://f-droid.org/packages/ara.memoryguardian/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Take Control of Your Clipboard
A Small App for Enhanced Privacy & SecurityMemory Guardian is a lightweight Android app that enhances user privacy and security by automatically clearing the clipboard at set intervals. This helps protect sensitive information, like passwords, from potential leaks to other applications.
https://f-droid.org/packages/ara.memoryguardian/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv


28.04.202513:27
Implement Auto-Delete Clipboard History to Prevent Sensitive Data Leaks
I copy passwords from my password manager all the time (I use KeePass, so they're long and complex), and I know a lot of people do the same. How is it that Samsung’s clipboard saves everything in plain text with no expiration? That’s a huge security issue.
I even tried switching to Gboard (Google’s keyboard), thinking that would help, but nope, everything I copied was still getting saved in Samsung’s clipboard. Turns out the clipboard functionality is tightly integrated with One UI, so it doesn’t matter what keyboard you use, your clipboard history still gets stored in plain text.
https://us.community.samsung.com/t5/Suggestions/Implement-Auto-Delete-Clipboard-History-to-Prevent-Sensitive/td-p/3200743
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
I copy passwords from my password manager all the time (I use KeePass, so they're long and complex), and I know a lot of people do the same. How is it that Samsung’s clipboard saves everything in plain text with no expiration? That’s a huge security issue.
I even tried switching to Gboard (Google’s keyboard), thinking that would help, but nope, everything I copied was still getting saved in Samsung’s clipboard. Turns out the clipboard functionality is tightly integrated with One UI, so it doesn’t matter what keyboard you use, your clipboard history still gets stored in plain text.
https://us.community.samsung.com/t5/Suggestions/Implement-Auto-Delete-Clipboard-History-to-Prevent-Sensitive/td-p/3200743
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv


16.05.202507:45
Government webmail hacked via XSS bugs in global spy campaign
Hackers are running a worldwide cyberespionage campaign dubbed 'RoundPress,' leveraging zero-day and n-day flaws in webmail servers to steal email from high-value government organizations.
ESET researchers who uncovered the operation attribute it with medium confidence to the Russian state-sponsored hackers APT28 (aka "Fancy Bear" or "Sednit").
https://www.bleepingcomputer.com/news/security/government-webmail-hacked-via-xss-bugs-in-global-spy-campaign/
https://www.welivesecurity.com/en/eset-research/operation-roundpress/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Hackers are running a worldwide cyberespionage campaign dubbed 'RoundPress,' leveraging zero-day and n-day flaws in webmail servers to steal email from high-value government organizations.
ESET researchers who uncovered the operation attribute it with medium confidence to the Russian state-sponsored hackers APT28 (aka "Fancy Bear" or "Sednit").
https://www.bleepingcomputer.com/news/security/government-webmail-hacked-via-xss-bugs-in-global-spy-campaign/
https://www.welivesecurity.com/en/eset-research/operation-roundpress/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202507:56
Alleged Data Exposure Hits Indonesian Supreme Court
Reports circulating online suggest that a database purportedly belonging to the Supreme Court of the Republic of Indonesia (mahkamahagung.go.id) has been exposed. The alleged breach reportedly involves a dataset containing detailed information related to various courts across the country and the individuals associated with them.
Analysis of sample data circulating in connection with the alleged exposure indicates the presence of structured records. This data appears to encompass not only personal and professional contact information but also various identifiers and timestamps.
https://dailydarkweb.net/alleged-data-exposure-hits-indonesian-supreme-court/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Reports circulating online suggest that a database purportedly belonging to the Supreme Court of the Republic of Indonesia (mahkamahagung.go.id) has been exposed. The alleged breach reportedly involves a dataset containing detailed information related to various courts across the country and the individuals associated with them.
Analysis of sample data circulating in connection with the alleged exposure indicates the presence of structured records. This data appears to encompass not only personal and professional contact information but also various identifiers and timestamps.
https://dailydarkweb.net/alleged-data-exposure-hits-indonesian-supreme-court/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202508:03
Malicious npm Package Leverages Unicode Steganography, Google Calendar as C2 Dropper
Cybersecurity researchers have discovered a malicious package named "os-info-checker-es6" that disguises itself as an operating system information utility to stealthily drop a next-stage payload onto compromised systems.
"This campaign employs clever Unicode-based steganography to hide its initial malicious code and utilizes a Google Calendar event short link as a dynamic dropper for its final payload," Veracode said in a report shared with The Hacker News.
https://thehackernews.com/2025/05/malicious-npm-package-leverages-unicode.html
https://www.veracode.com/resources/sophisticated-npm-attack-leveraging-unicode-steganography-and-google-calendar-c2
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Cybersecurity researchers have discovered a malicious package named "os-info-checker-es6" that disguises itself as an operating system information utility to stealthily drop a next-stage payload onto compromised systems.
"This campaign employs clever Unicode-based steganography to hide its initial malicious code and utilizes a Google Calendar event short link as a dynamic dropper for its final payload," Veracode said in a report shared with The Hacker News.
https://thehackernews.com/2025/05/malicious-npm-package-leverages-unicode.html
https://www.veracode.com/resources/sophisticated-npm-attack-leveraging-unicode-steganography-and-google-calendar-c2
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202507:35
Coinbase says customers’ personal information stolen in data breach
Crypto giant Coinbase has confirmed its systems have been breached and customer data, including government-issued identity documents, were stolen.
In a legally required filing with U.S. regulators, Coinbase said a hacker this week told the company that they had obtained information about customer accounts and demanded money from the company in exchange for not publishing the stolen data.
https://techcrunch.com/2025/05/15/coinbase-says-customers-personal-information-stolen-in-data-breach/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Crypto giant Coinbase has confirmed its systems have been breached and customer data, including government-issued identity documents, were stolen.
In a legally required filing with U.S. regulators, Coinbase said a hacker this week told the company that they had obtained information about customer accounts and demanded money from the company in exchange for not publishing the stolen data.
https://techcrunch.com/2025/05/15/coinbase-says-customers-personal-information-stolen-in-data-breach/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv


28.04.202513:18
Coinbase 2FA error fixed after many believed their account was hacked
The crypto exchange fixed a confusing flaw
The two-factor authentication (2FA) error on Coinbase, one of the biggest cryptocurrency trading platforms in the world, was finally fixed.
In early April, Coinbase customers started noticing that their Account Activity logs showed “2-step verification failed” entries. These would suggest that someone tried to log in using valid credentials but was only stopped after entering the wrong 2FA code.
https://www.techradar.com/pro/security/coinbase-2fa-error-fixed-after-many-believed-their-account-was-hacked
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
The crypto exchange fixed a confusing flaw
The two-factor authentication (2FA) error on Coinbase, one of the biggest cryptocurrency trading platforms in the world, was finally fixed.
In early April, Coinbase customers started noticing that their Account Activity logs showed “2-step verification failed” entries. These would suggest that someone tried to log in using valid credentials but was only stopped after entering the wrong 2FA code.
https://www.techradar.com/pro/security/coinbase-2fa-error-fixed-after-many-believed-their-account-was-hacked
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202508:10
Attack claimed by pro-Ukraine hackers reportedly erases a third of Russian court case archive
A cyberattack on Russia's national case management and electronic court filing system wiped out about a third of its case archive, according to a report by the Russian Audit Chamber.
The system, known as “Pravosudiye” (meaning “justice” in Russian), was hacked last October and was down for a month, disrupting the operation of Russian court websites, communication networks, and email services.
https://therecord.media/russia-court-system-hack-third-of-case-files-deleted
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
A cyberattack on Russia's national case management and electronic court filing system wiped out about a third of its case archive, according to a report by the Russian Audit Chamber.
The system, known as “Pravosudiye” (meaning “justice” in Russian), was hacked last October and was down for a month, disrupting the operation of Russian court websites, communication networks, and email services.
https://therecord.media/russia-court-system-hack-third-of-case-files-deleted
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202508:14
A ransomware gang hacked the Gloucester County, VA local government
Ransomware gang BlackSuit today claimed responsibility for an April 2025 data breach of the Gloucester County, Virginia local government.
Gloucester County officials first announced their offices experienced a network disruption on April 22. A day later, it said connectivity issues limited staff access to emails and disrupted operations.
https://www.comparitech.com/news/a-ransomware-gang-hacked-the-gloucester-county-va-local-government/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Ransomware gang BlackSuit today claimed responsibility for an April 2025 data breach of the Gloucester County, Virginia local government.
Gloucester County officials first announced their offices experienced a network disruption on April 22. A day later, it said connectivity issues limited staff access to emails and disrupted operations.
https://www.comparitech.com/news/a-ransomware-gang-hacked-the-gloucester-county-va-local-government/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
16.05.202508:19
Xoxo to Prague
Welcome to this week’s edition of the Threat Source newsletter.
I haven’t been to Prague in a while, which is a pity. It’s a wonderful city — great people, amazing food. I’ve visited customers there, held team meetings at the local office (shoutout to Petr!) and spent some memorable summer days off. But none of those are why I’m sending my greetings this time.
Last week, anyone trying to access LockBit’s dark web affiliate panels was greeted by a defaced page with the message:
"Don't do crime CRIME IS BAD xoxo from Prague”
https://blog.talosintelligence.com/xoxo-to-prague/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Welcome to this week’s edition of the Threat Source newsletter.
I haven’t been to Prague in a while, which is a pity. It’s a wonderful city — great people, amazing food. I’ve visited customers there, held team meetings at the local office (shoutout to Petr!) and spent some memorable summer days off. But none of those are why I’m sending my greetings this time.
Last week, anyone trying to access LockBit’s dark web affiliate panels was greeted by a defaced page with the message:
"Don't do crime CRIME IS BAD xoxo from Prague”
https://blog.talosintelligence.com/xoxo-to-prague/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv


28.04.202514:08
iOS and Android juice jacking defenses have been trivial to bypass for years
New ChoiceJacking attack allows malicious chargers to steal data from phones.
About a decade ago, Apple and Google started updating iOS and Android, respectively, to make them less susceptible to “juice jacking,” a form of attack that could surreptitiously steal data or execute malicious code when users plug their phones into special-purpose charging hardware. Now, researchers are revealing that, for years, the mitigations have suffered from a fundamental defect that has made them trivial to bypass.
https://arstechnica.com/security/2025/04/ios-and-android-juice-jacking-defenses-have-been-trivial-to-bypass-for-years/
https://krebsonsecurity.com/2011/08/beware-of-juice-jacking/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
New ChoiceJacking attack allows malicious chargers to steal data from phones.
About a decade ago, Apple and Google started updating iOS and Android, respectively, to make them less susceptible to “juice jacking,” a form of attack that could surreptitiously steal data or execute malicious code when users plug their phones into special-purpose charging hardware. Now, researchers are revealing that, for years, the mitigations have suffered from a fundamental defect that has made them trivial to bypass.
https://arstechnica.com/security/2025/04/ios-and-android-juice-jacking-defenses-have-been-trivial-to-bypass-for-years/
https://krebsonsecurity.com/2011/08/beware-of-juice-jacking/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv

28.04.202513:11
Google confirms that Driving Mode has been removed from Google Assistant
Google has officially announced that it has removed Assistant Driving Mode from Google Maps on Android. This is part of a broader transition to its new AI initiative, Gemini.
First introduced in 2019, the Driving Mode function had undergone several updates and refinements over the years, but it is no longer accessible within the Google Maps app, according to a report from 9to5Google.
https://www.ghacks.net/2025/04/28/google-confirms-that-driving-mode-has-been-removed-from-google-assistant/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
Google has officially announced that it has removed Assistant Driving Mode from Google Maps on Android. This is part of a broader transition to its new AI initiative, Gemini.
First introduced in 2019, the Driving Mode function had undergone several updates and refinements over the years, but it is no longer accessible within the Google Maps app, according to a report from 9to5Google.
https://www.ghacks.net/2025/04/28/google-confirms-that-driving-mode-has-been-removed-from-google-assistant/
📡@cRyPtHoN_INFOSEC_IT
📡@cRyPtHoN_INFOSEC_FR
📡@cRyPtHoN_INFOSEC_EN
📡@cRyPtHoN_INFOSEC_DE
📡@BlackBox_Archiv
अधिक कार्यक्षमता अनलॉक करने के लिए लॉगिन करें।